|
Getting your Trinity Audio player ready... |
Multiple China-linked advanced persistent threat (APT) groups have exploited a critical zero-day vulnerability in SAP NetWeaver Visual Composer, identified as CVE-2025-31324, according to EclecticIQ analysts. The breach has impacted critical infrastructure and enterprise networks worldwide.
Unpatched SAP Flaw Enables Deep System Compromise
The vulnerability allows for unauthenticated file uploads, granting attackers remote code execution (RCE) capabilities. This enables them to gain deep access to systems, maintain persistence, and execute commands remotely. Open directories on attacker-controlled servers revealed logs of at least 581 compromised SAP NetWeaver systems.
Global Campaign and Attack Methods
Read More: Cyber Incident at Nova Scotia Power Exposes Customer Data and Disrupts IT Systems
The campaign has been linked to Chinese state-affiliated groups UNC5221, UNC5174, and CL-STA-0048, with threat intelligence support from Mandiant and Palo Alto Networks. Attackers performed widespread internet scans using tools like Nuclei to identify vulnerable SAP endpoints.
Their command-and-control (C2) infrastructure, particularly the IP address 15.204.56[.]106, stored logs and exploit results, showcasing the scale of the operation.
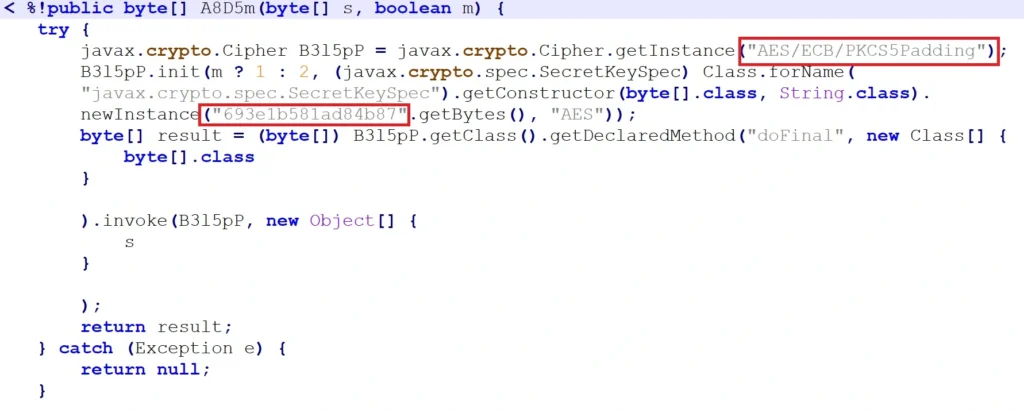
Webshell Deployment for Persistence and Command Execution
Following exploitation, the attackers deployed customized webshells to maintain access:
- coreasp.js – A variant of the Behinder webshell encrypted with AES/ECB, allowing in-memory execution without disk traces.
- forwardsap.jsp – A lightweight, unauthenticated shell enabling quick command execution.
These webshells were uploaded through the vulnerable /developmentserver/metadatauploader API endpoint, offering persistent access while evading detection.
Targeted Sectors Include Energy, Healthcare, and Government
The attackers focused on industries crucial to national security and public welfare, including:
- UK natural gas and water utilities
- US medical device manufacturers and oil exploration companies
- Saudi government ministries
The strategic targeting of SAP NetWeaver, often linked to Industrial Control Systems (ICS), raises significant risks of espionage and disruption.
Detailed Threat Group Activities
- CL-STA-0048: Utilized TCP reverse shells and DNS beaconing for remote control, communicating with the domain sentinelones[.]com.
- UNC5221: Deployed KrustyLoader malware, downloaded from Amazon S3, to install Sliver backdoors for stealthy persistence.
- UNC5174: Delivered SNOWLIGHT downloader to initiate VShell RAT, providing in-memory control through SAP endpoints.
These groups used advanced reconnaissance, network mapping, and cloud exploitation, leveraging vulnerabilities in VMware ESXi hypervisors for lateral movement.
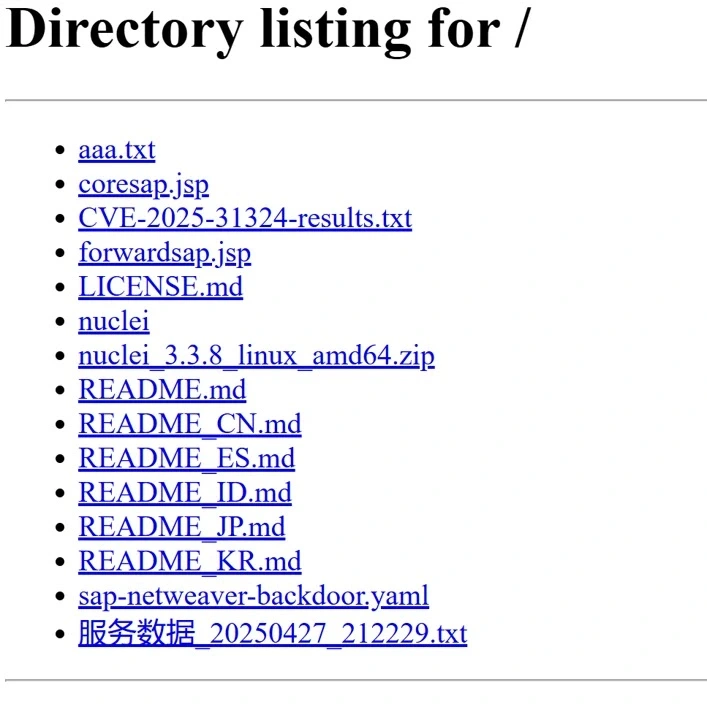
Security Recommendations and Mitigation
Immediate application of SAP Security Note #3594142 is advised. For systems where patching is not possible, SAP suggests removing vulnerable components and restricting API exposure.
Organizations should conduct:
- Threat hunting for unauthorized webshells and suspicious file uploads.
- Network monitoring for outbound connections to identified C2 infrastructure.
- Log analysis of web access and process activity for anomalies.
Indicators of Compromise (IOCs)
Security teams are urged to cross-check their environments against known IOCs linked to the campaign to prevent further exploitation
| Threat Actor/Cluster | IOC Type | Value/Details |
|---|---|---|
| Unattributed China Nexus (scanning C2) | IP | 15.204.56[.]106 |
| SHA256 | 4c9e60cc73e87da4cadc51523690d67549de4902e880974bfacf7f1a8dc40d7d | |
| SHA256 | 63aa0c6890ec5c16b872fb6d070556447cd707dfba185d32a2c10c008dbdbcdd | |
| CL-STA-0048 (reverse shell/DNS beaconing) | IP/Domain | 43.247.135[.]53 (sentinelones[.]com, TCP 10443) |
| Domain | aaa.ki6zmfw3ps8q14rfbfczfq5qkhq8e12q.oastify.com | |
| IPs | 54.77.139[.]23, 3.248.33[.]252 | |
| UNC5221 (KrustyLoader malware) | S3 domains | applr-malbbal.s3.ap-northeast-2.amazonaws[.]com |
| S3 domains | abode-dashboard-media.s3.ap-south-1.amazonaws[.]com | |
| S3 domains | brandnav-cms-storage.s3.amazonaws[.]com | |
| SHA256 | f92d0cf4d577c68aa615797d1704f40b14810d98b48834b241dd5c9963e113ec | |
| SHA256 | 3f14dc65cc9e35989857dc1ec4bb1179ab05457f2238e917b698edb4c57ae7ce | |
| UNC5174 (SNOWLIGHT/VShell/GOREVERSE) | IP | 103.30.76[.]206 (TCP 443) |
| SHA256 | 00920e109f16fe61092e70fca68a5219ade6d42b427e895202f628b467a3d22e | |
| SHA256 | 2dcbb4138f836bb5d7bc7d8101d3004848c541df6af997246d4b2a252f29d51a | |
| Aliyun object | ocr-freespace.oss-cn-beijing.aliyuncs.com/2025/config.sh | |
| General (victim SAP systems) | IPs (examples) | 45.155.222[.]14, 159.65.34[.]242, 138.68.61[.]82, 192.243.115[.]175 |
| Webshell files | helper.jsp, forwardsap.jsp, coreasp.js, .webhelper.jsp, 404_error.jsp |




