|
Getting your Trinity Audio player ready... |
May 13, 2025 – A serious software supply chain attack has been exposed after cybercriminals compromised RVTools, a trusted utility used widely in VMware environments. The attackers transformed the installer into a delivery vehicle for the Bumblebee malware, a dangerous loader known to open the door for ransomware attacks and advanced post-exploitation toolkits.
Malicious Activity Detected by Microsoft Defender
Microsoft Defender first flagged the incident for Endpoint, which raised a high-confidence alert when an employee attempted to install RVTools in a corporate setting. The security system detected a suspicious version.dll file running from the same directory as the installer—an abnormal behavior that immediately suggested tampering.
Deep Dive into the Malware
RVTools, a longstanding favorite among IT administrators, had no prior association with malicious activity. A hash verification of the installer revealed discrepancies between the file downloaded and the checksum posted on RVTools’ official website.
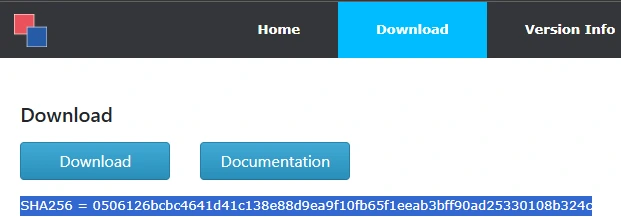
Further investigation using VirusTotal confirmed the file’s malicious nature. Thirty-three out of 71 antivirus engines detected it as a variant of the Bumblebee malware loader, an advanced threat often used to establish initial access before launching ransomware or tools like Cobalt Strike.
Security researchers found the malware to be heavily obfuscated. The file metadata included unusual descriptors, such as “Hydrarthrus” as the original filename and bizarre product names like “nondimensioned yogis” and “ungroupable clyfaker gutturalness”—likely inserted to confuse analysts and obscure the malware’s purpose.
Containment and Response
Swift action was taken. Analysts confirmed that only the most recent installer had been compromised. Older versions matched their official hash values and were found to be clean. Submissions of the malicious installer to public platforms surged globally before the RVTools website was taken offline for emergency remediation.
Shortly after, the site was restored with a clean installer. File size and hash values returned to their legitimate states, indicating a targeted and time-limited breach.
Microsoft Defender successfully isolated the malware on the affected system, and there were no signs of further lateral movement. Security teams across the organization conducted comprehensive audits, validating other installations and sharing indicators of compromise (IOCs) with peers and law enforcement.
Lessons from a Breach
This incident illustrates the increasing threat posed by software supply chain attacks—even those involving tools trusted by cybersecurity professionals. It reinforces the need for file integrity checks, real-time threat intelligence sharing, and close inspection of metadata during installation.
Experts also point to the importance of secure software distribution practices. Vendors are urged to adopt measures like strict code signing, HTTPS-only downloads, and immutable file hosting to prevent similar compromises in the future.
RVTools has since restored its legitimate installer, but security teams are advised to review any recent installations and monitor systems for unauthorized execution of version.dll.
As cyber threats continue to evolve, this case serves as a sharp reminder that vigilance is essential—even for seemingly routine downloads.
Indicators of Compromise (IOC)
| Artifact | Details |
|---|---|
| Malicious DLL | version.dll (in same directory as RVTools installer) |
| Malicious Hash | Mismatched with official hash listed on RVTools website |
| Metadata | Original File Name: Hydrarthrus |
| Company: Enlargers pharmakos submatrix | |
| Product: nondimensioned yogis | |
| Description: elephanta ungroupable clyfaker gutturalness | |
| Detection Name | Bumblebee Loader variant |
| AV Detection | 33/71 engines on VirusTotal |
| Timeline | May 13, 2025 – Discovery and remediation |