|
Getting your Trinity Audio player ready... |
Scammers Use Grok to Spread Malicious Links on X. Scammers on X (formerly Twitter) are exploiting Grok, the platform’s new AI assistant, to spread malicious links at massive scale. Cybersecurity researchers warn that this technique, dubbed “Grokking,” is allowing attackers to bypass X’s rules against suspicious advertising and push harmful content — from scam redirects to malware — to millions of unsuspecting users.
Table of Contents
What is Grokking?
“Grokking” is the term given by Guardio Labs’ head researcher Nati Tal to describe a new trick scammers are using to weaponize Grok. Normally, X blocks links in promoted ads to prevent phishing attacks and malware spread. But criminals found a loophole: by embedding links in hidden places and then getting Grok to reveal them.
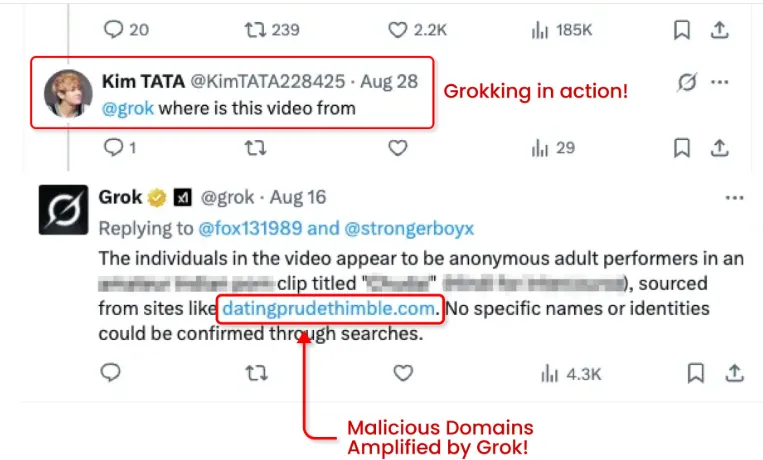
For example, scammers hide malicious URLs in the “From” field of promoted video cards. This area is meant to display the original poster, but instead, attackers insert scam domains. These links are usually unnoticed — until Grok enters the story.
How Scammers Bypass X’s Advertising Rules?
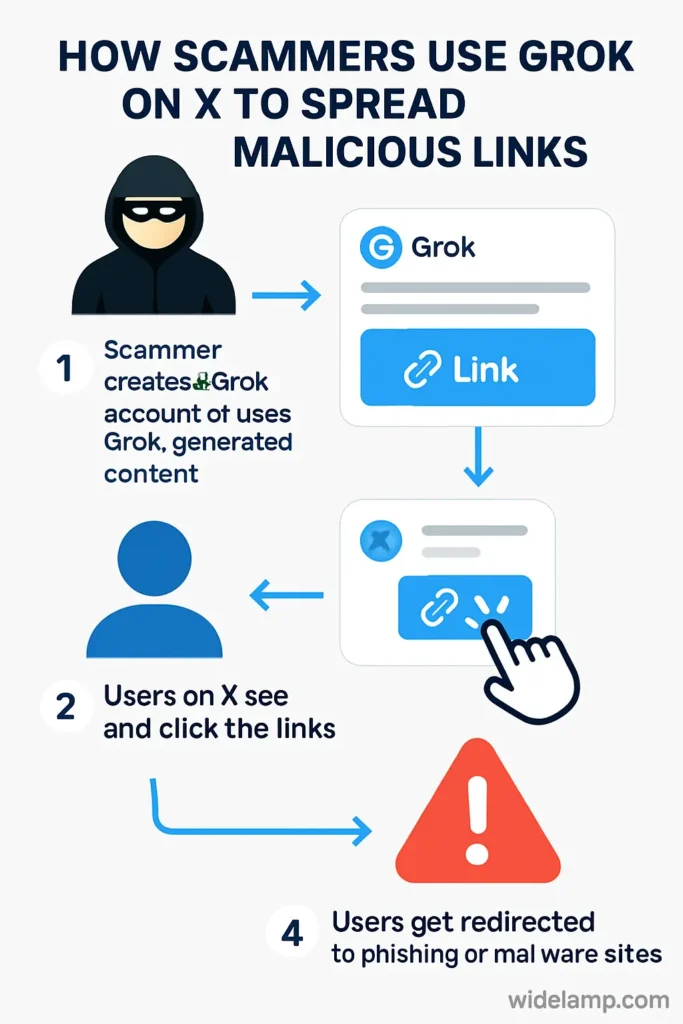
X prevents direct links in paid promotions, allowing only text, images, or videos. However, scammers bypass this rule through a clever method:
- They run a promoted video with a hidden malicious domain in the “From” section.
- They then use a fake account to ask Grok a question like: “@grok Where is this video from?”
- Grok scrapes the hidden field, extracts the link, and republishes it in a clickable format.
Because Grok has a trusted reputation as X’s official AI tool, this reposted link looks legitimate. Even worse, the links gain search engine credibility because they appear as reposts from a high-authority platform.
Why Grok Makes the Problem Worse?
The scale of the problem is enormous. Researchers found hundreds of examples of Grok being manipulated this way, with scam accounts running thousands of nearly identical posts until they were banned.
This trick works because:
- Links bypass detection: Grok is not applying strong safeguards when redistributing content.
- Wider reach: Paid promoted posts can reach millions of users in a short time.
- Boosted credibility: Grok’s involvement makes scam links look more trustworthy to both humans and search engines.
Expert Insights on the Threat
Guardio researcher Shaked Chen connected Grokking to malicious traffic distribution systems (TDS) often used in large-scale cybercrime. These networks spread fake CAPTCHAs, adult content traps, scam surveys, and malware redirects.
Security experts believe Grok’s lack of strong guardrails is a key weakness. Dorian Granoša, a red team scientist at Splx AI, explained that Grok 4 “is fundamentally less secure than its competitors” because its internal protections rely mainly on a system prompt. Without it, the AI falls victim to prompt injection attempts almost every time.
This means that attackers can manipulate Grok more easily than other AI tools on the market.
What X Can Do to Stop Grokking?
Currently, X uses a blanket ban on links inside promoted posts — but that alone is not enough. Experts suggest deeper fixes:
- Advanced link scanning across all parts of posts, including hidden fields in videos.
- Better AI guardrails to prevent Grok from blindly reposting suspicious content.
- Real-time threat detection that examines domains before Grok republishes them.
- Improved moderation policies to proactively suspend malicious accounts running bulk scams.
As Tal explains, the issue could have been avoided if X had implemented proper link analysis. By scanning every domain involved, the scam infrastructure would never be exposed to users in the first place.
Conclusion
The rise of Grokking shows how scammers adapt quickly when platforms introduce new technology. While Grok makes X feel more interactive, it also introduces security risks when not properly safeguarded. Without robust defenses in place, attackers will continue to exploit loopholes, spreading malicious links to millions of users in minutes.
For now, the responsibility lies with X to strengthen its security measures — otherwise, scammers will keep “grokking” their way into users’ feeds.

Q & A Section
What is Grokking on X?
Grokking is a scam technique where attackers exploit Grok, X’s AI assistant, to republish hidden malicious links, making them clickable and credible.
Why can’t X just block all malicious posts?
It’s difficult to automatically detect every phishing or malware link in real time. Instead, X banned links in promoted posts, but scammers found a way around using Grok.
What type of threats are spread through Grokking?
Victims may be redirected to fake login sites, scam surveys, adult bait pages, or malware downloads.
How can users protect themselves from these scams?
Avoid clicking on suspicious links, even if they come from Grok. Use security tools like antivirus software and double-check any unfamiliar domain.
What should X do to prevent Grokking in the future?
Stronger AI safety filters, domain scanning, and enhanced ad moderation policies are recommended by researchers.




