|
Getting your Trinity Audio player ready...
|
If you’re looking for a powerful, automated solution for reconnaissance in cybersecurity, ReconFTW tools feature and commands might be one of the best open-source tools available today. Let’s explore the key features and commands that make ReconFTW stand out for penetration testers, bug bounty hunters, and cybersecurity enthusiasts.
Table of Contents
What Is ReconFTW?
ReconFTW is an open-source reconnaissance framework designed to fully automate the discovery and vulnerability assessment phase during penetration tests or bug bounty engagements. By chaining together a variety of robust security tools and methodologies, ReconFTW helps you discover subdomains, scan for vulnerabilities, and gather deep intelligence quickly and efficiently
Read More: Top 10 Open Source Reconnaissance Tools for Bug Bounty Hunters
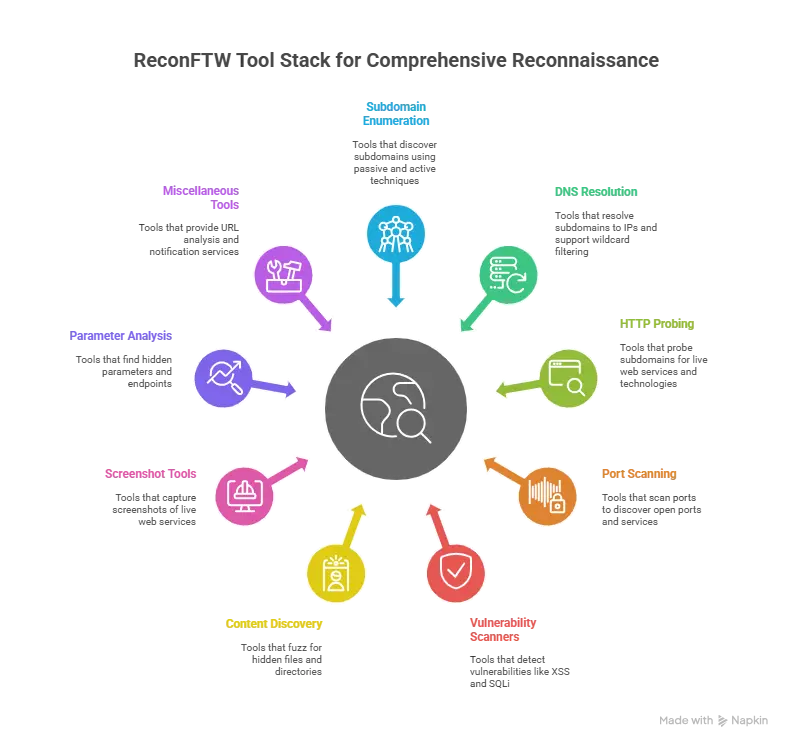
ReconFTW Tools Feature and Commands: An Overview
Main Features
ReconFTW goes far beyond basic subdomain enumeration. Here are some standout features you should know: Reconftw tools feature and commands
Subdomain Enumeration: Uses a mix of passive, brute-force, permutation, certificate transparency, analytics, and DNS record techniques for comprehensive results
Vulnerability Checks: Automated testing for common flaws like:
- XSS
- Open Redirects
- SSRF
- CRLF Injection
- LFI
- SQL Injection
- SSTI
- SSL Misconfigurations
- DNS Zone Transfers
OSINT Integration: Utilizes open-source intelligence to find extra information about the target—social profile links, leaked credentials, and more.
Web Prober & Screenshotting: Fast identification of live web assets and screenshot capture for reporting.
Nuclei Integration: Template-based vulnerability scanning for countless known CVEs and misconfigurations.
Port Scanning: Quickly checks for open ports with tools like Naabu.
Directory Fuzzing & Dorking: Finds hidden resources and sensitive files using search engine dorks.
Pattern & Parameter Discovery: Searches for URL patterns and hidden parameters to help find bugs like XSS.
Standalone Module Support: Ability to run submodules (subdomains, port scanning, web fuzzing) independently.
Custom Output Structure: Saves results in organized folders for each scan or target
Core Commands & Usage Examples
ReconFTW keeps things simple with a command-line interface. Here are the most common and useful commands, with explanations:
| Command Structure | Purpose | Example Usage |
|---|---|---|
-d <domain> | Specify a single domain target | ./reconftw.sh -d example.com -r |
-l <file> | Use a file with a list of targets | ./reconftw.sh -l targets.txt -r |
-m <company> | Multi-domain (entity with several domains) | ./reconftw.sh -m org -l domains.txt -r |
-i <file> | Include in-scope subdomains | ./reconftw.sh -d site.com -i in.txt -r |
-x <file> | Exclude out-of-scope subdomains | ./reconftw.sh -d site.com -x oos.txt -r |
-r | Full recon mode | ./reconftw.sh -d example.com -r |
-a | Active scan with all features | ./reconftw.sh -d example.com -a |
-s | Run only subdomain scanning | ./reconftw.sh -d example.com -s |
-w | Perform only web-related scans | ./reconftw.sh -d example.com -w |
-g | Run Google Dorking | ./reconftw.sh -d example.com -g |
--deep | Enable deeper, resource-intensive scans | ./reconftw.sh -d example.com -r --deep |
-o <directory> | Custom output directory | ./reconftw.sh -l targets.txt -r -o /output/ |
-h | Display help and all available options | ./reconftw.sh -h |
You can tailor scans to your target and time constraints, mix options, or run individual modules for more targeted assessments
Read More: Cyber Insurance Costs Fall, but Protection Remains Essential for Business Strength
Why Use ReconFTW?
- Saves Time: ReconFTW automates and accelerates tedious manual tasks.
- Accuracy & Depth: By chaining industry-standard tools, it delivers broad and deep recon results.
- Flexible for All Use Cases: Whether you’re conducting a quick survey or a detailed investigation, ReconFTW scales with your needs.
- Community Supported: Open-source with active development and frequent updates.
Getting Started
Setting up ReconFTW is a fast and user-friendly process. Here’s how you can get started in just a few steps, along with the exact commands you’ll need.
1. Clone the ReconFTW Repository
First, open your terminal and clone the ReconFTW project from GitHub:
git clone https://github.com/six2dez/reconftw.git
2. Change Into the ReconFTW Directory
Navigate into the cloned repository:
bashcd reconftw
3. Install Dependencies
ReconFTW comes with an installation script that handles dependencies for most common Linux distributions.
bash./install.sh
This will automatically check and install the required tools and dependencies.
4. Give Execute Permission to the Script (if needed)
If you get a permissions error, make the main script executable:
bashchmod +x reconftw.sh
5. Run a Basic ReconFTW Scan
Test your installation by running a basic scan. Replace example.com with your target domain:
bash./reconftw.sh -d example.com -r
This command launches a full reconnaissance scan against the specified domain using ReconFTW’s automated features.
Commonly Used Startup Commands Table
| Command | Description |
|---|---|
git clone https://github.com/six2dez/reconftw.git | Download the latest ReconFTW code |
cd reconftw | Enter the ReconFTW project folder |
./install.sh | Install requirements and dependencies |
chmod +x reconftw.sh | Grant script execution permission |
./reconftw.sh -d example.com -r | Run a full scan against a domain |
Best Practices With ReconFTW
- Always review your included and excluded subdomain lists to avoid targeting out-of-scope assets.
- Consider using the
--deepflag on a VPS for more in-depth coverage. - Regularly update the tool and its dependencies for optimal results and latest scanning capabilities.